
As organizations seek to leverage AI and big data analytics to drive efficiencies in their operations through “smart networks,” IT and OT networks are converging. In a word, these complex industrial control systems are now connected to the internet, making them vulnerable to hacking. Because many of these industrial control systems were not designed with cybersecurity in mind, it’s not surprising they draw hackers’ attention when these older systems are connected to... Read More
Increasingly, enterprises and their employees are incorporating practices to make access to data more fluid. The increase in BYOD (bring your own device) policies, in addition to threats targeting mobile device access and networks, create multiple endpoint vulnerabilities.
In addition, employees working from home or connecting to Wi-Fi networks to work on-the-go means that the enterprise network security perimeter is more porous... Read More


Cloud security, also known as cloud computing security, consists of a set of policies, controls, procedures and technologies that work together to protect cloud-based systems, data and infrastructure. These security measures are configured to protect data, support regulatory compliance and protect customers' privacy as well as setting authentication rules for individual users and devices. From authenticating access to filtering traffic, cloud security can be... Read More
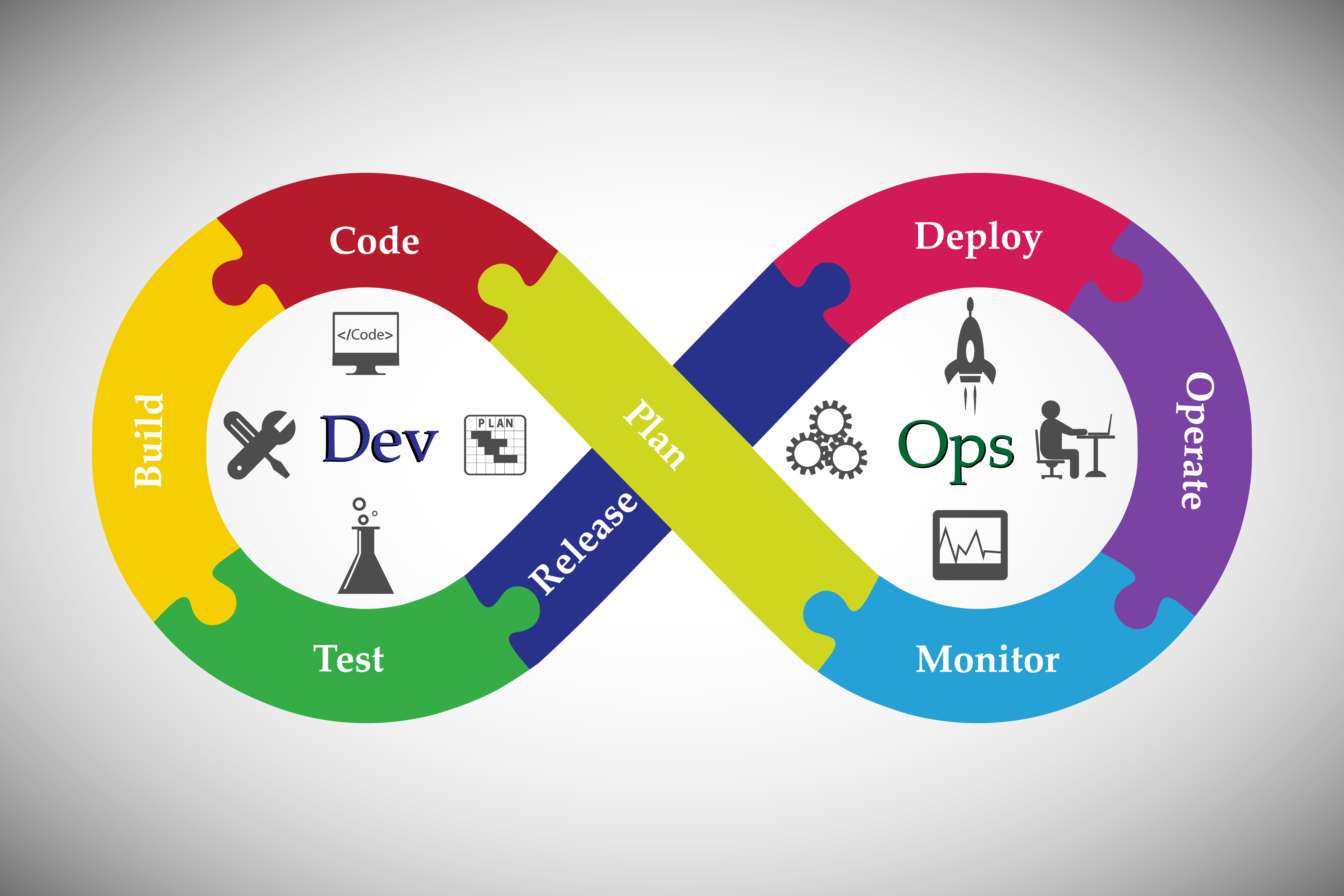
DevOps is a set of practices that automates the processes between software development and IT teams, in order that they can build, test, and release software faster and more reliably. The concept of DevOps is founded on building a culture of collaboration between teams that historically functioned in relative siloes. The promised benefits include increased trust, faster software releases, ability to solve critical issues quickly, and better manage unplanned work.
It's a firm... Read More


Compliance was meant to be a floor, but it has become a ceiling. Industry standard certifications and compliance frameworks (for example, HIPPA, PCI, ISO) are the bare minimum and intended to be generic. A framework can’t account for the nuances of your company operations and environment. These audits only look at a snapshot in time, not the ongoing state of your security. Your company could pass an audit, but a day later a vulnerability could be left unaddressed and your security... Read More

To ensure that a web application is secure you have to identify all security issues and vulnerabilities within the web application itself before a malicious hacker identifies and exploits them. That is why it is very important that the web application vulnerabilities detection process is done throughout all of the SDLC stages, rather than once the web application is live.
There are several different ways to detect vulnerabilities in web applications. You can scan the web application... Read More
